Google Zero Trust Security

What is zero trust security.
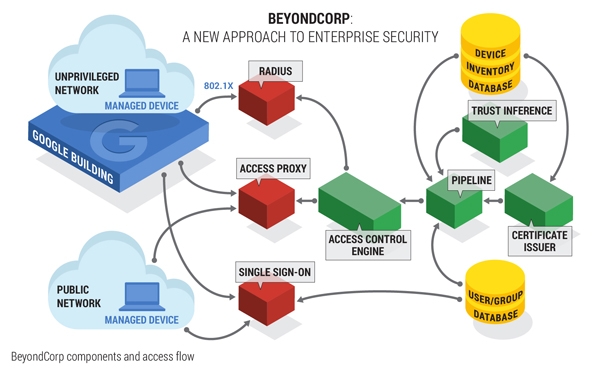
Google zero trust security. Google was among the first companies to embrace the zero trust security model a new approach built around the idea that enterprises should not inherently trust any user or network and that any attempt to access a business system or application must always be verified before any level of access is granted. Beyondcorp is a zero trust security framework modeled by google that shifts access controls from the perimeter to individual devices and users. Once on the network users including threat actors and malicious insiders are free to move laterally and access or exfiltrate whatever data they are not limited to. The zero trust model recognizes that trust is a vulnerability.
In 2009 google s beyondcorp initiative pioneered the corporate application of zero trust security after state sponsored cyberattacks revealed the limitations of castle and moat approaches to security. Google zero trust security framework goes beyond passwords google outlines how beyondcorp determines whether a device should be allowed to access an application in a perimeter less network. This week google expanded the same philosophy to machines workloads and services. In 2014 google unveiled beyondcorp its zero trust approach to user access and authentication.
The zero trust security model is a framework that involves shifting access controls from the perimeter to individual devices and users allowing employees to work securely from any location. The end result allows employees to work securely from any location without the need for a traditional vpn. Increasingly companies are turning to a zero trust framework to address the complexity of today s security risks. Remember the point of infiltration of an attack is often not the target location.
Beyondcorp is a zero trust security framework that shifts access controls from the perimeter to individual devices and users allowing employees to work securely from any location without the need for a traditional virtual private network.